Phishing Attacks: How University Members Can Protect Themselves
26 October 2023, by Newsroom editorial office
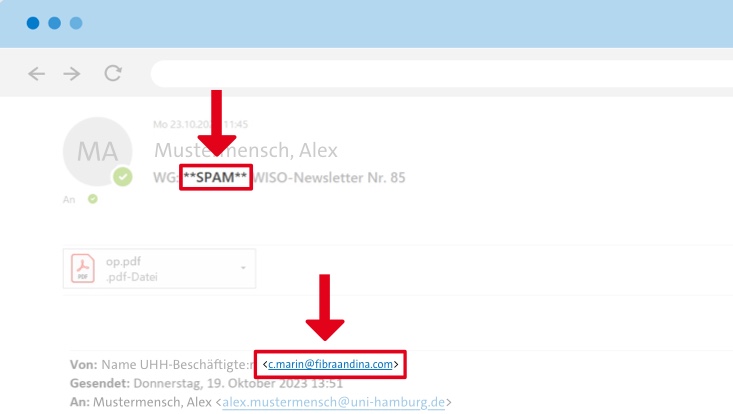
Photo: Universität Hamburg
Faculty newsletters are also being used; although only some of the emails are directly marked as “**SPAM**”. Do not open attachments under any circumstances.

Photo: Universität Hamburg / Vogiatzis
Phishing aims to obtain the uni usernames and associated passwords of University members, especially with the use of fraudulent mails.
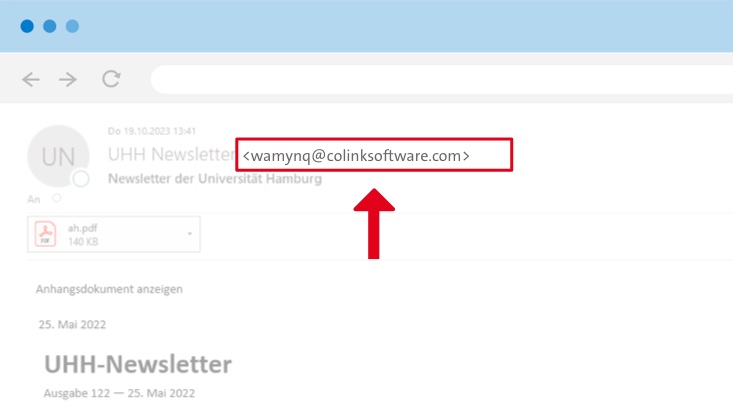
Photo: Universität Hamburg
Currently, older newsletter issues, among other things, are being used for phishing emails. While the sender name is correct in such emails, the sender address shows that it is fraudulent.

Photo: Universität Hamburg
Faculty newsletters are also being used; although only some of the emails are directly marked as “**SPAM**”. Do not open attachments under any circumstances.

Photo: Universität Hamburg / Vogiatzis
Phishing aims to obtain the uni usernames and associated passwords of University members, especially with the use of fraudulent mails.

Photo: Universität Hamburg
Currently, older newsletter issues, among other things, are being used for phishing emails. While the sender name is correct in such emails, the sender address shows that it is fraudulent.

Photo: Universität Hamburg
Faculty newsletters are also being used; although only some of the emails are directly marked as “**SPAM**”. Do not open attachments under any circumstances.
Universities are also targets for hackers. Currently, Universität Hamburg is facing another wave of phishing mails. University members need to be especially vigilant. The most important questions and answers at a glance.
What is phishing?
Phishing efforts primarily take place via email. They aim to trick the recipient into clicking on a link or opening an email attachment. These types of emails look authentic due to, for example, the use of a known and genuine-looking sender and/or a convincingly worded letter. Emails from mailboxes that have already been hacked are often used to lead recipients to believe that they are authentic.
The link used in a phishing email usually leads to a convincing phishing page and requests your username and password. The data is then gathered and used to take over the inbox and the data.
Often, the emails have an attachment—preferably in an Office format such as Word or Excel. Opening these installs malware that is also used to gather login data and can lead to the theft of saved files.
All staff members of Universität Hamburg, from students and teaching staff to administrative employees, are targets. Thus, we all need to be vigilant to minimize such attacks in the long term. Phishing mails are not the only problem: beware of text messages, WhatsApp, etc. and phony phone calls.
How do I recognize phishing?
In many cases, mails are recognized as spam and marked accordingly in the subject line. Phishing mails, however, are becoming more and more professional, making them hard to detect at first glance.
Often, the sender name provides a University affiliation, but the sender email address does not match— If you are not paying close attention, you could miss this.
Another scam sees the mails come from compromised email addresses, because the affected accounts often use University-wide circulars (e.g., the Executive University board circular on the current semester), which can lend greater credibility in further phishing campaigns. Highly valuable and/or administrative login data may then be accessed. If messages are sent from an already-compromised mail account, they will not be marked as spam in the subject line and they may even refer to earlier correspondence.
What phishing efforts do we currently know about?
Various emails are always in circulation. Among other things, newsletters that have already been sent from the University Administration or the faculties are re-sent with a fake sender name. They give the impression that they are new newsletters; however, they contain malicious PDF attachments and can be recognized only by the incorrect sender address.
Furthermore, there are additional supposed messages that appear to come from individuals or institutions at the University. The mails contain fake links to a replicated login page of Outlook Web Access (OWA) from Microsoft Exchange. Do not provide your login details!
An often-used ploy is a notification that the Outlook inbox is full and urging recipients to click on a link to remedy the problem.
How can I protect myself?
The most important thing is to remain vigilant when handling emails, text messages, or phone calls! Almost everyone will have to deal at some point or other with these kinds of attacks. Be especially wary if you are asked to act immediately.
In case your password does fall into the wrong hands, here is an important tip: store your mobile number via user administration. This will ensure that you receive help more quickly if your user account is blocked and that you can be provided with a new one-time password.
-
Check the sender address
carefully read your emails and check the sender address.
-
Set up a digital signature
This signature tells you if the email really comes from an internal sender—namely, through the red seal symbol. If you click on this, you will find more information about the signature and its validity. This allows you to determine if the mail is trustworthy or not. The more Universität Hamburg members set up digital signatures, the more secure email correspondence becomes!
Tip: Contact the Regional Computing Center to find out about personal certificates, which enable you to create digital signatures. You can use this signature for greater security.
-
Check links
Links should also always be checked. By mousing over,” which means skimming your mouse over the link without clicking on the link, you can see where the link leads to. The most important thing here is the first part of the address provided. Even if “uni-hamburg” is part of a long link, always look at the beginning of the link address. “uni-hamburg” must come before the first single slash ( / ).
Correct: https://www.kus.uni-hamburg.de/de.html
Incorrect: hxxps://mialhamidiyyahpancur[.]sch.id/hh/hh/hh/webmail.chemie.uni-hamburg.de.html
Therefore, always look for the first single slash in the address: this will lead you onto the right path!
As a general rule, before typing in your uni username and your password on a web page, check the address line in the internet browser to see if it’s really a University page—for example, to use a University service or mail program.
-
Investigate further and do not reveal passwords!
If you receive spam or suspicious emails, do not under any circumstance click on attachments or links—simply delete the mail. If you are uncertain, ask the sender via telephone or zoom if they really sent the mail.
Phone calls can also be a means for deception. Here, too, you must be vigilant—never provide access data or passwords via telephone. Nobody, not even the Regional Computing Center, will ask you to provide passwords via telephone.
How do I know if I have been the victim of a phishing attack?
There may be several clues. For example, if colleagues ask you about spam mails sent from your account. If strange activities at your user account have been registered—for example, an unusually high number of mails sent—it will be blocked administratively. You can then no longer log in with your access data.
What should I do if I have been the victim of a phishing attack?
If you think that you have accidentally entered your uni username and password into a fraudulent website, change your password immediately via user administration. This is the only way to change passwords.
Contact the Regional Computing Center (RRZ) by email at rrz-serviceline"AT"uni-hamburg.de or by telephone on +49 40 42838-7790. If personal data is being stolen, the data protection officer and the Legal Unit also need to be involved. The RRZ will support them accordingly.
If you have opened or downloaded a malicious attachment, contact the RRZ by email at rrz-serviceline"AT"uni-hamburg.de or by telephone on +49 40 42838-7790.
And most importantly: don’t be ashamed. The attacks are now frequently highly professional. One wrong click may be all it takes. You are the victim and are in no way at fault.
Where can I report spam mails?
If you have received a phishing email, send it to rrz-serviceline"AT"uni-hamburg.de and it-sicherheit"AT"uni-hamburg.de as an email attachment. Doing so warns the RRZ and allows it to take further action.
Be sure not to simply forward the phishing email but rather attach it to a new email (e.g., by drag and drop in Outlook), as this is the only way to check the email header.


